Managed Security Service Provider (MSSP)
Topics
The MSSP mode allows the user to effectively manage sources collected throughout the system. The source can be defined as a host providing data to the system. When the MSSP mode is enabled, sources are continuously gathered and monitored so they can be displayed in an understandable way. This document outlines MSSP licensing, source collection, state management, multi-tenant architecture, usage tracking, and operational workflows.
Collecting Sources
The sources are collected in two ways - by the Network Probe or the Logserver itself. The Network Probe utilizes a unique set of fields against documents of different technologies to generate an inimitable identifier. This makes it possible to determine from which source the data came and therefore also to manage the system’s traffic.
Managing Sources
Only admin-level users can manage sources in the Config plugin. For such users, it displays the Sources tab in the side navigation bar, the Sources tab in the Config plugin, and a blue banner at the top of the screen.
Sources tab in the navigation bar
Sources tab in the Config plugin
Blue banner
Source Types
Two states of sources can be distinguished - Waiting and Allowed.
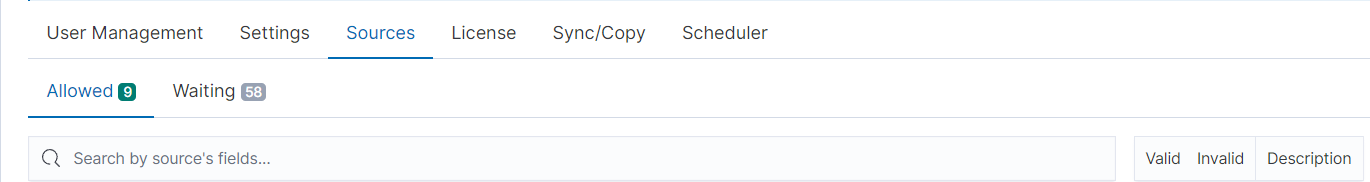
Sources types
1. Waiting
The Waiting source is a source pending approval. Data related to this source will not be ingested until it is accepted. Only the first document from a given source is collected and stored as an example. Its details include information such as when it was indexed, the source from where it was sent, and its contents. In addition, a note can be added to distinguish it from other sources and describe it in a memorable way.
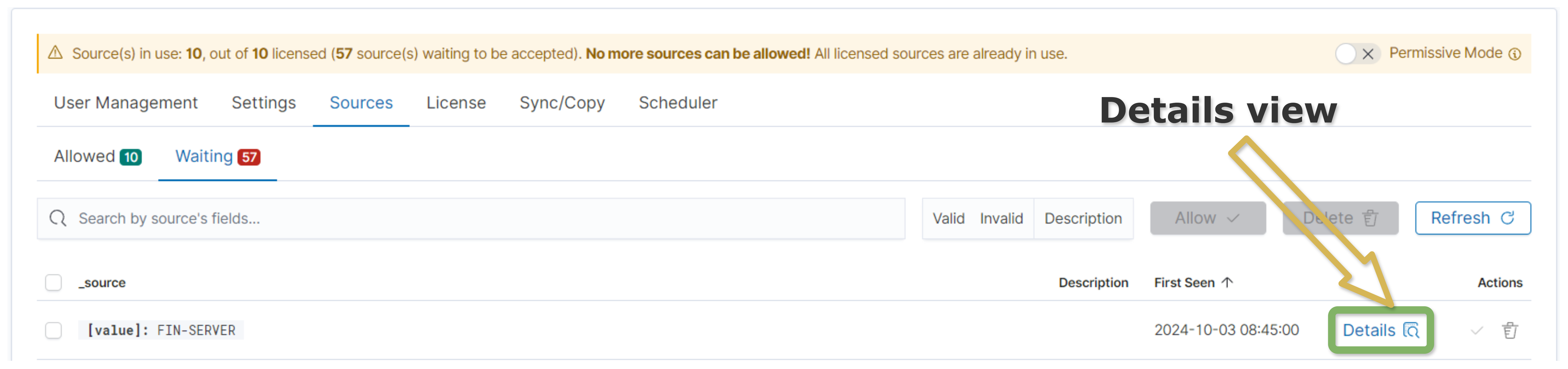
2. Allowed
When a Waiting document is Allowed, the flow of its data is made possible, and the source consumes license allocation, enabling full processing and monitoring.
Source Removal
Both types of sources can be removed. After deleting the Waiting source, if the data is still coming in, after a brief moment the source will reappear in the table with the possibility of possible acceptance. On the other hand, if an Allowed source is deleted, the data will stop coming in, although the data collected up to the time of deletion will not be cleared.
Manual Change of State from Waiting to Allowed
Check the box of the sources which you want to move from
WaitingtoAllowedstate.Press on the button
Allow.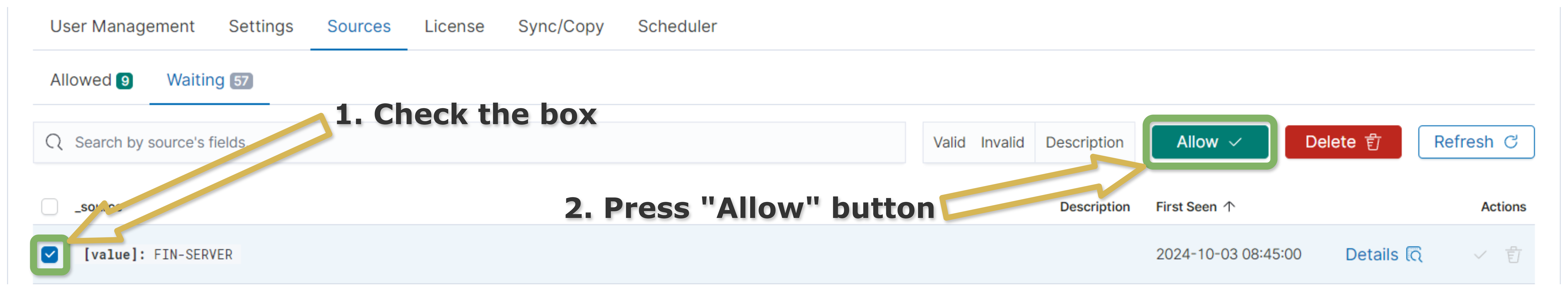
A details of the operation will be displayed. If you still want to perform the operation, press
Yes, allowbutton.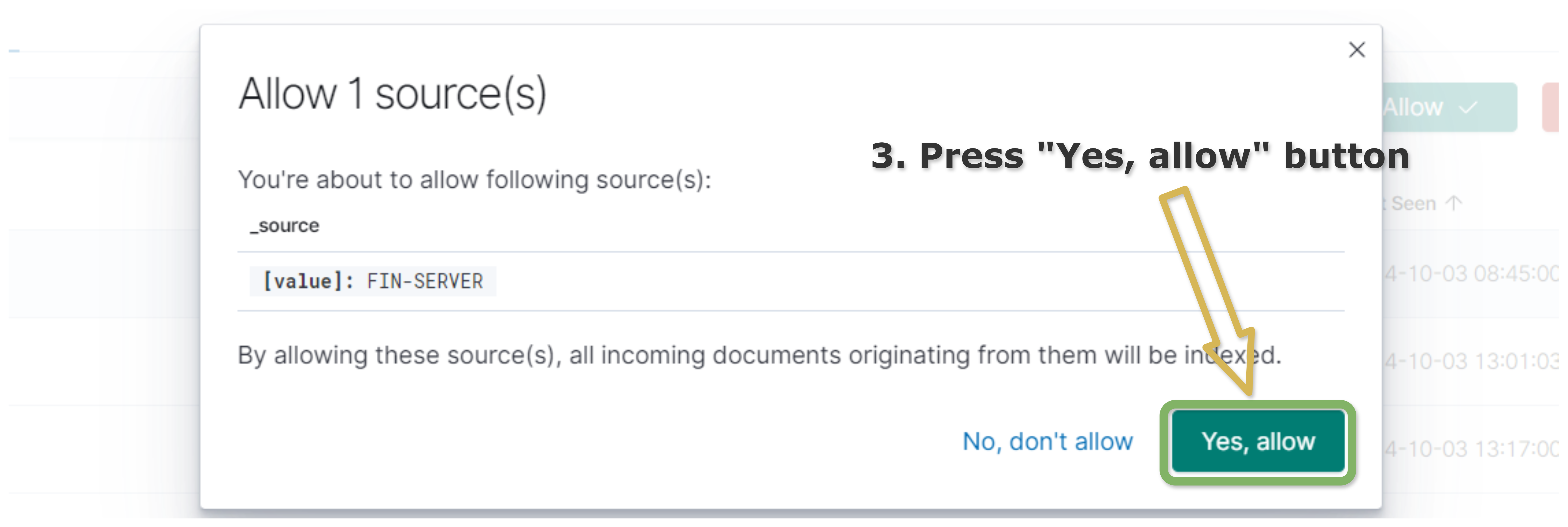
Manual Change of State from Allowed to Waiting
Go to the
Allowedtab.Check the box of the sources which you want to move from
AllowedtoWaitinglist.Press on the button
Delete.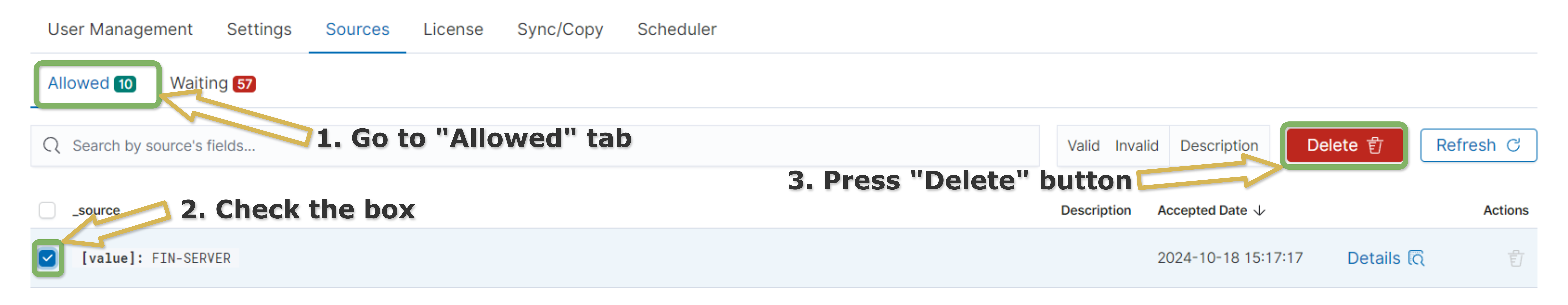
Details of the operation will appear. If you still want to perform the operation, press
Yes, deletebutton.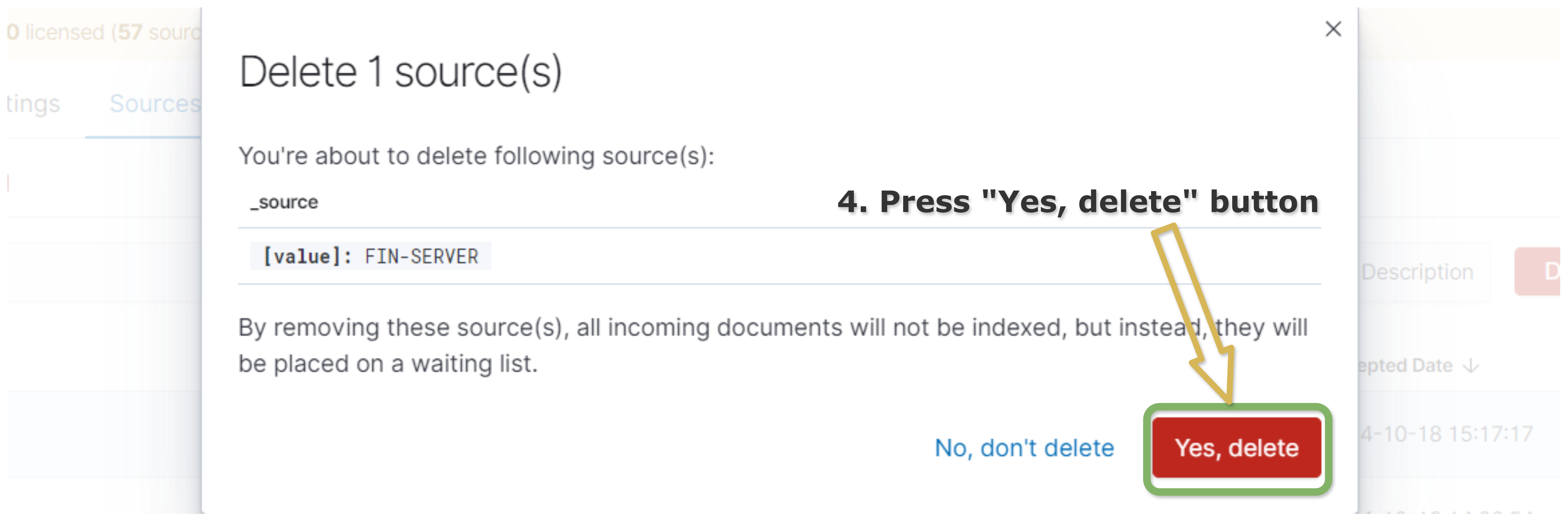
Fingerprint
The Network Probe generates a unique identifier for each document called a fingerprint in the _mssp_id field. Fingerprint is encrypted data from the document. Sources without fingerprints are automatically dropped. Sources whose fingerprints cannot be decrypted are placed on a waiting list but without the possibility of being allowed. Documents with valid fingerprints are placed on a waiting list with the possibility of approval until the license limit is reached.
The Permissive Mode
The Permissive Mode is enabled out of the box. It automatically allows waiting sources until the license limit is completely used. If all available sources have been used, no others will be accepted, which is also indicated by the blue banner changing to orange with a warning. The purpose of this transition is to draw the user’s attention to checking whether all allowed sources are still being used. If so, it means that a licence covering more sources should be purchased.
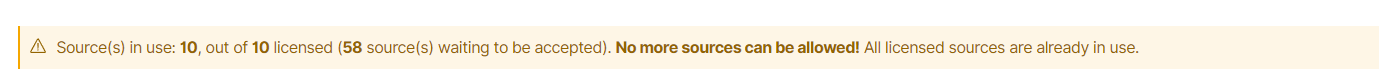
Orange banner
It was introduced to make it easier to use the system, without having to worry and remember about source management. On the other hand, if there is a need to allow or remove troublesome or erroneous sources manually, it is always possible to disable this mode and perform manual operations.
Turn On/Off the Permissive Mode
Go to the Sources tab.
Toggle the switch located on the blue bar captioned
Permissive Modeto the state in which you want it to work.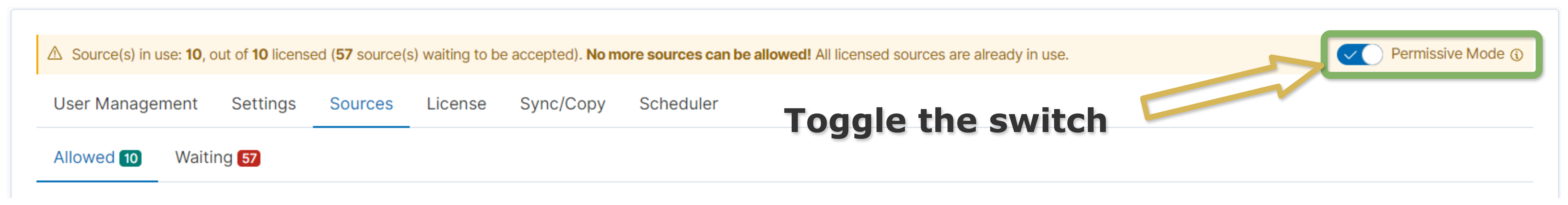
Check MSSP Status
Go to the Config tab in the navigation bar.
Select Licence section in the top bar.
The value of the
MSSPfield in Licence Details indicates the status of the module.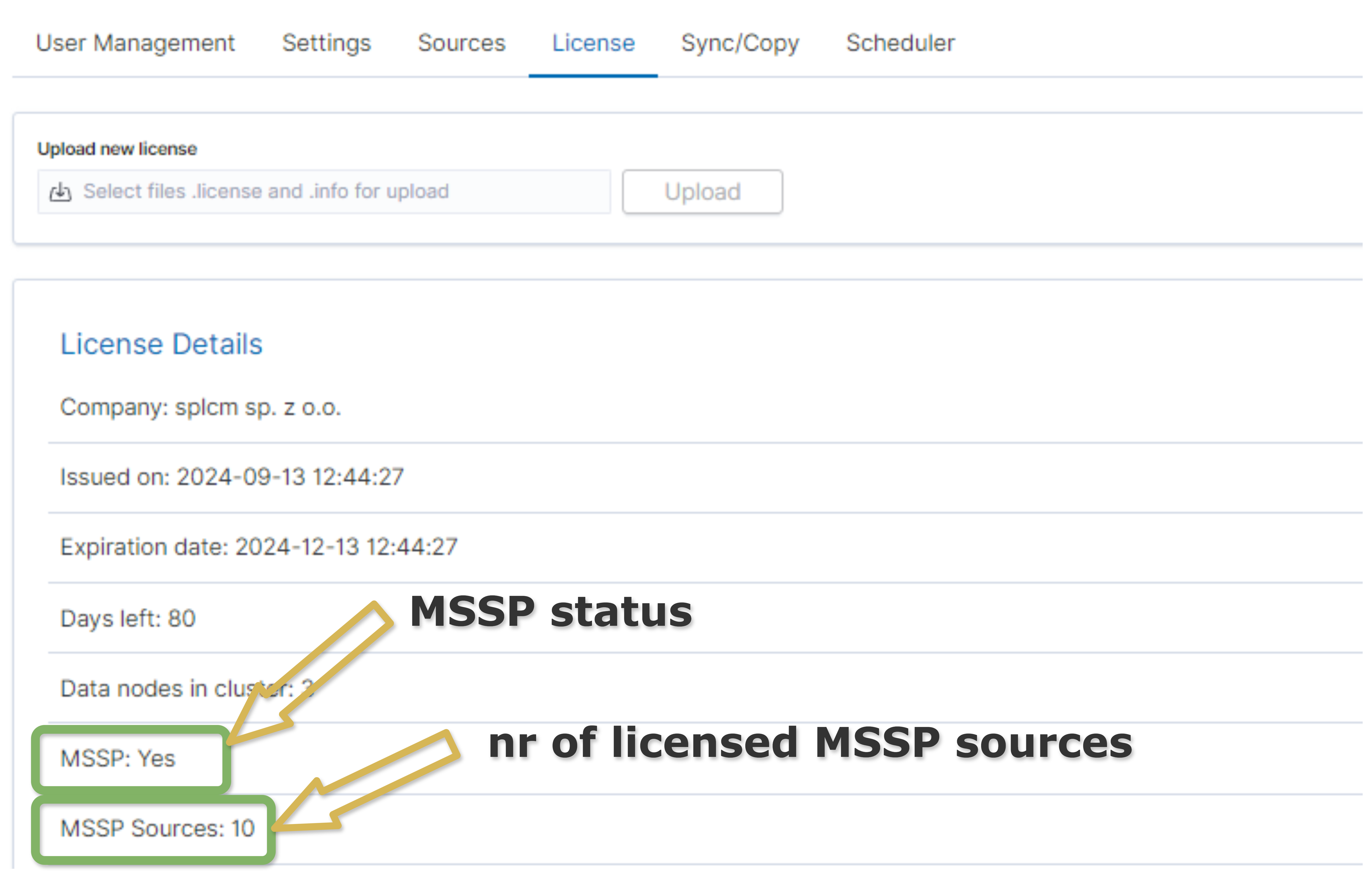
MSSP Disabled
When MSSP mode is disabled, the system still gathers information about sources based on documents, but it does not block or reject any incoming documents. A list of sources can still be viewed in the Config->Sources tab.
Multi-Tenant Architecture
Energylogserver SIEM provides a robust multi-tenant architecture to ensure customer isolation and security:
Data Isolation – Separate indices per customer with encryption at rest, ensuring no data leakage between tenants.
Network Isolation – VLAN/VPC segmentation to segregate customer traffic.
Authentication Isolation – Dedicated authentication realms per customer for secure access control.
Resource Isolation – CPU, memory, and storage quotas allocated per tenant to guarantee performance.
This architecture supports centralized management through a provider console while offering customer-specific self-service portals.
Usage Tracking and Billing
The system provides comprehensive usage tracking to support transparent billing and capacity planning:
Event Count – Tracks the number of events processed per customer.
Data Volume – Measures total bytes ingested per source.
Active Sources – Monitors the number of sources consuming license allocation.
Service Tiers
MSSP operations support multiple service tiers to meet diverse customer needs:
service_tiers:
basic:
source_limit: 50
storage_quota_gb: 500
retention_days: 90
sla_uptime: 99.0
professional:
source_limit: 200
storage_quota_gb: 2000
retention_days: 365
sla_uptime: 99.5
enterprise:
source_limit: 1000
storage_quota_gb: 10000
retention_days: 2555 # 7 years
sla_uptime: 99.9
Customer Lifecycle Management
The MSSP system supports end-to-end customer management workflows:
Onboarding:
Initial Assessment – Gather requirements and plan integrations (2 business days).
Environment Setup – Provision customer space and configure sources (3 business days).
Testing and Validation – Verify data flow and performance (2 business days).
Go-Live – Activate production environment and provide training (1 business day).
Ongoing Management:
Daily Tasks – Health monitoring, source management, alert triage.
Weekly Tasks – SLA review, capacity planning, customer communication.
Monthly Tasks – Billing generation, performance optimization.
Offboarding:
Data retention for 90 days with export options (JSON, CSV, Parquet).
Secure cleanup of customer data and access revocation.
SLA Monitoring
The system provides real-time SLA monitoring to ensure service quality:
Availability – Targets 99.9% uptime, measured monthly.
Data Ingestion – Targets 99.5% successful ingestion, measured daily.
Alert Response Time – Targets 5 minutes for critical alerts, with severity-based thresholds.
Query Performance – Targets 2-second average query response time, measured hourly.
Performance Optimization
To maintain optimal performance, administrators can run optimization scripts:
#!/bin/bash
# Optimize customer indices
optimize_customer_performance() {
local CUSTOMER_ID=$1
curl -X POST "https://els.company.com:9200/security-events-$CUSTOMER_ID-*/_forcemerge?max_num_segments=1"
echo "Performance optimization completed for customer $CUSTOMER_ID"
}